DevSecOps for Leaders
An executive breakdown for secure software delivery
Table of contents
DevSecOps for Leaders
Introduction
In a world where security is a top priority, DevSecOps has emerged as one of the most successful ways to ensure that your company's digital assets are protected. At its core, DevSecOps is an approach to software development that uses principles and techniques from both development and security.
What is DevSecOps?
DevSecOps, as it's called, is a culture of collaboration between development, operation, and security teams. It is not just a tool or process; DevSecOps is a way to build secure software faster. The goal of DevSecOps is to move away from the traditional waterfall model of software development where security reviews are performed at the end of each phase in the project lifecycle and instead integrate security into all aspects of software development so that it becomes part of every team's day-to-day activities. This approach helps organizations achieve continuous delivery and continuous improvement goals by reducing time-to-market for new features or products, increasing quality assurance within a single code base, minimizing downtime when issues arise, and reducing costs associated with manual testing processes such as QA cycles or postmortem reviews after issues have occurred.
Why build a DevSecOps culture?
Improve security. Security should be built into your organization's development process, which means you need to hire the right people and give them the tools they need to work with the rest of your team. You'll also want to make sure that developers are aware of any new security risks their code could introduce, so they can take action before it becomes an issue for your customers or users.
Increase customer satisfaction. If customers don't trust you as a company, then they won't do business with you again—or even worse, they may tell others not to buy from you either! A culture focused on DevSecOps will help improve this situation by making sure all employees have access to information about how their work impacts security across every layer of their product's stack: from cloud, cluster, container, & code and everything in between.
Increase customer retention rates by reducing negative experiences associated with using your application/service (e., downtime caused by system crashes)
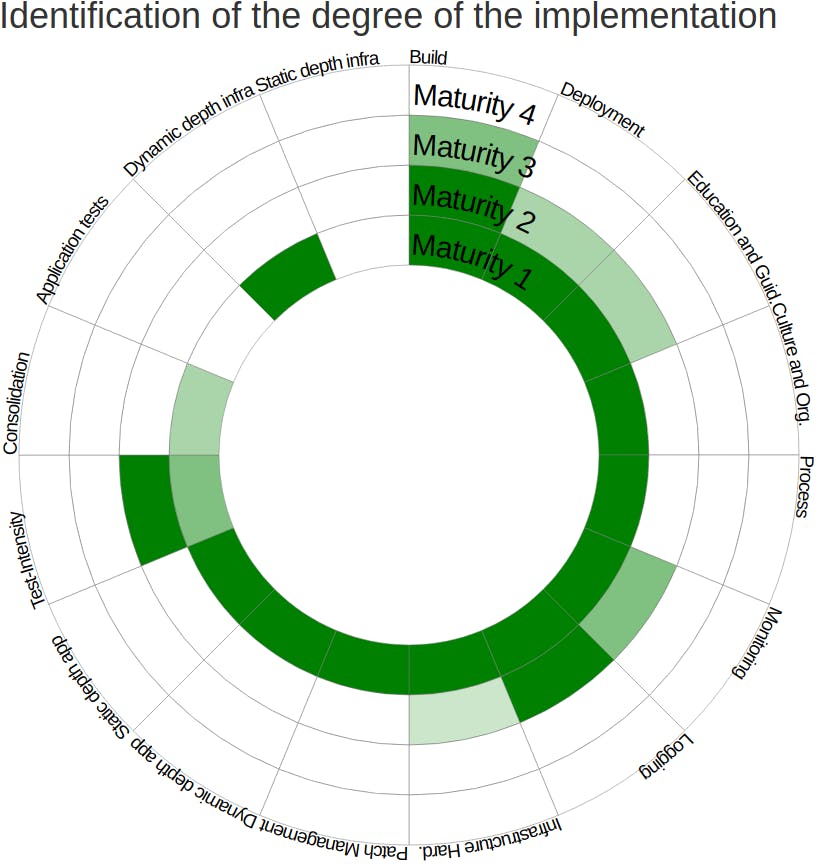
DevSecOps Maturity Model
The DEVSecOps Maturity Model is an essential tool for leaders to assess the maturity of their organization's DevSecOps practices. The model can also be used by developers and security professionals to evaluate their own workflows, as well as operations teams who play a key role in the success of DevSecOps initiatives.
Levels of maturity per https://owasp.org/www-project-devsecops-maturity-model/
Level 1: Basic understanding of security practices
Level 2: Adoption of basic security practices
Level 3: High adoption of security practices
Level 4: Advanced deployment of security practices at scale
Testing is key to modern application security.
Testing is key to modern application security. It's not enough to fix bugs when you find them; you have to find them before your customers do. The only way to do that is by testing proactively and automatically, with a focus on the most important functionality of your application and it's dependencies.
Pairing DevSecOps teams with traditional QA groups is one way of making sure this happens, but it's not the only one. An effective DevSecOps strategy will put testing first, using automation and tooling in conjunction with manual processes (such as threat modeling) for maximum effectiveness.
Here are some common testing methods used by the community:
DAST (dynamic application security testing)
Dynamic application security testing (DAST) is a type of testing that is performed at runtime, in contrast to static analysis. DAST doesn't require source code access and can be used to find vulnerabilities in web applications.
A DAST tool can be either manual or automatic. Manual DAST involves logging into an application's UI and performing actions by hand, while automatic DAST involves detecting flaws by automatically sending requests to the API endpoint of a program and monitoring the responses received from it.
CAST (Control and Audit Software Testing)
The CAST process is simple and involves the following steps:
Control: This is a policy or procedure that has been defined to ensure that all systems are configured securely. It can either be implemented directly into your code, put in place by a security team, or simply documented somewhere.
Audit: After implementing controls like encryption and password management, you will want to make sure they are being followed properly. For example, if you have an encrypted database server but your developers aren’t using encryption keys when accessing it from their laptops then this would be considered not being compliant with that control. You need to find out what’s really happening! That’s where auditing comes in.
Test: This step ensures that there is some type of validation before moving forward with something new—a test should tell us whether we can proceed or not (and why). For example, let's say I'm writing some code for my company's next product release which requires third party libraries; I would run tests against them first so I know exactly what functionality they provide and if any issues exist before integrating them into my project codebase."
SAST (Static Application Security Testing)
SAST (Static Application Security Testing) is a static analysis tool that analyzes source code to find vulnerabilities.
It's a good first step in the SDLC and can help you find common vulnerabilities like SQL injection, cross-site scripting and path traversal. However, it falls short of dynamic testing because it can only find known vulnerabilities.
Conclusion
There are many ways to start with DevSecOps. It can be a challenge to find the right tools, but it is worth it in the end. The best way to get started is by researching what you need and testing it out before implementing into your company’s software development lifecycle (SDLC). or hire a consultant to help you out :D Cheers friends and stay secure!


